DomainKeys and Domain Keys Identified Mail (DKIM) are cryptographic authentication solutions that add signatures to email messages, allowing recipient sites to verify that the message was sent by an authorized sender and not altered in transit.
DomainKeys
DomainKeys is an email authentication system that verifies an email sender's DNS domain and the integrity of the message. DomainKeys is not part of Simple Mail Transfer Protocol (SMTP) routing. It operates on the RFC 2822 message and not the SMTP envelope defined in RFC 2821. For more information about RFC2822 and RFC2821, see the Terminology section below.
DomainKeys authentication adds a header named 'DomainKey-Signature' that contains a digital signature. The default parameters for the authentication mechanism use SHA-1 as the cryptographic hash and RSA as the public key encryption scheme and encode the encrypted hash using Base64. For more information about SHA-1 and Base64, see the Terminology section below.
The receiving SMTP server uses the email's originating domain name, the 'string _domainkey' and a selector (which allows a domain to have more than one public-key in the DNS) from the header to perform a DNS lookup. The returned data includes that domain's public key. The receiver decrypts this data (the hash value) in the header field and simultaneously recalculates the hash value for the received mail body from the point immediately following the DomainKey-Signature header. If the two values match, this cryptographically proves that the mail did originate from the specified domain with no tampering in transit.
For example, DomainKeys confirms to the recipient that an email message from "example.net" is indeed from "example.net". It cannot, however, identify whether the email from "example.net" is spam or not. The presence of a signature does not guarantee whether a message is spam since spammers are able to sign email messages using DomainKeys.
DKIM
DKIM builds on the DomainKeys authentication in the form of Domain Keys Identified Mail, Authenticated Sender, Meta-Mail, etc. DKIM is a mechanism by which emails are cryptographically signed, permitting a signing domain to claim responsibility for the introduction of a message into the mail stream. The responsible organization then adds a digital signature to the message associating it with a domain name for the organization. After the email is signed, any agent in the message transit path can validate the signature. Message recipients can verify the signature by directly querying the signer's domain to retrieve the appropriate public key. They can then confirm the email was certified by an organization who possesses the private key for the signing domain.
DKIM is compatible with existing DomainKeys (DK) DNS records, meaning a DKIM module does not automatically require additional DNS administration. DKIM enhances the DK DNS key record to permit the addition of several parameters. DKIM uses a different RFC2822 [RFC2822] header named DKIM-Signature for storing the signature to distinguish it from DomainKeys.
Overview of the Feature
Connect provides the ability to enable or disable signing outgoing e-mail messages using DomainKeys/DKIM technology. Connect adds a header named DomainKey-Signature (for DomainKeys) or DKIM-Signature (for DKIM) that contains a digital signature.
Connect Approach to Support DomainKeys/DKIM
Administrators need to configure the various receiver domains using Connect. While configuring a receiver domain, Administrators must specify the private key from the public or private key pair generated by the domain owner. This private key will be used to sign outgoing emails. The corresponding public key must be stored in the DNS Server as a TXT record with various defined attributes.
Connect determines whether to sign the outgoing email based on parameters configured for your installation and then signs the message accordingly. Connect supports signing outgoing messages with DomainKeys using the simple or nofws algorithm as well as DKIM using the simple algorithm. Connect adds a DomainKey-Signature header when using DomainKeys or DKIM-Signature when using DKIM in the outgoing emails. For more information about simple and nofws algorithms, see the Terminology section below.
The receiving SMTP server then queries the DNS server and verifies the digital signature. Once verified, the SMTP server delivers the email to the customer.
The following is an example of a typical DomainKey-Signature header:
DomainKey-Signature: a=rsa-sha1; s=jun2005.eng; d=example.com;
[email protected]; c=simple; q=dns;
b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSbav+yuU4zGeeruD00lszZVoG4ZHRNiYzR
- a: The algorithm used to generate the signature. The default is rsa-sha1, an RSA signed SHA1 digest. Signers and verifiers must support rsa-sha1.
- b: The signature data, encoded as a Base64 string
- c: The canonicalization algorithm. Verifiers must support simple and nofws. For more information about canonicalization algorithm, see the Terminology section below.
- d: The domain name of the signing domain
- q: The query method used to retrieve the public key
- s: The selector used to form the query for the public key
As a result, a DNS query is made to:
jun2005.eng._domainkey.example.com
The following is an example of a typical DKIM-Signature header.
DKIM-Signature: a=rsa-sha1; c=simple/simple; d=connectify-div.com; s=n1024;
t=1153444845;
h=From:Reply-To:To:Subject:Date:Message-ID:X-Mailer:Mime-Version:Content-Type;
b=qwMjKBRwXbvzwE7l6XShbZ7ZMMrZ0sllxJKL4D8FKUmZX5dOphH
Applicability for Mail Farm
The DomainKeys/DKIM compliance is applicable for Connect instances using either Direct Mail Sending (DMS) or Mail Farm. Administrators can turn off the DomainKeys/DKIM support at the application level if the Mail Farm is configured to sign outgoing emails using DomainKeys/DKIM.
Performance Overhead
There is additional overhead involved when DomainKeys/DKIM is used to sign outgoing emails from Connect.
When using the DomainKeys/DKIM feature, you are able to:
- Administer receiver domains
- Configure message signing
Administer Receiver Domains
Administrators can configure receiver domains with the appropriate details required to sign email messages. For more details about configuring receiver domains, see Administer Receiver Domains.
Configure Message Signing
Administrators can enable or disable signing at the system parameter-level, the conversation-level, or at the receiver domain-level. For more details about configuring message signing, see Message Signing at the Conversation Level.
DomainKeys/DKIM Support - Workflow
The following diagram illustrates the DomainKeys/DKIM workflow.
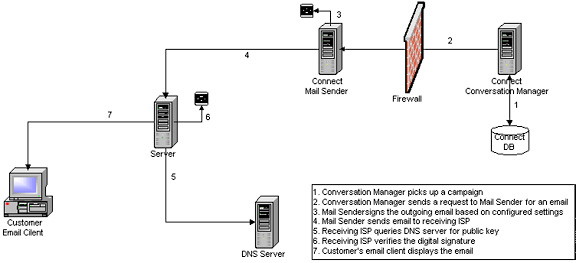
DomainKeys/DKIM Workflow
The DomainKeys/DKIM feature workflow is as follows:
- The Conversation Manager picks up a campaign
- The Conversation Manager requests the Mail Sender to send an email
- The Mail Sender signs the outgoing message based on the configured settings
- Identifies the sender's domain which is located in the From address of the outgoing email
- Determines if an email should be signed
- Selects a private-key (stored in the database)
- Performs Canonicalization of the email header and body
- Calculates the signature value
- Adds the DomainKey-Signature (or DKIM-Signature) header to the outgoing email
- The Mail Sender sends the email
- The Receiving ISP queries the DNS server for the public key
- The Receiving ISP verifies the digital signature
- The email message is delivered to the customer
Terminology
Base 64 - In computing, base64 is a data encoding scheme whereby binary-encoded data is converted to printable ASCII characters. It is defined as a MIME content transfer encoding for use in internet e-mail. The only characters used are the upper- and lower-case Roman alphabet characters (A-Z, a-z), the numerals (0-9), and the "+" and "/" symbols, with the "=" symbol as a special suffix code.
Canonicalization - The method used to prepare headers and content for presentation to the signing algorithm.
nofws Algorithm - A canonicalization algorithm (No Folding White Spaces) that tolerates common modifications as white-space replacement and header line re-wrapping.
RFC 2821 - Basic protocol specification for email transport.
RFC 2822 - Standard that describes the syntax for valid email addresses.
SHA-1 - This Secure Hash Algorithm takes a message of less than 264 bits in length and produces a 160-bit message digest designed so that it is computationally very difficult to find a text string that matches a given hash.
Simple Algorithm - A canonicalization algorithm that tolerates almost no modifications.
