If you cannot accept the occasional security breach, what is the alternative to ESPs?
On 1 April 2011, Epsilon disclosed that they had suffered a security breach and that a “subset” of their clients’ customer data had been exposed.

- Several experts observed that this breach will lead to a rash of targeted spear phishing attacks: since the attackers got customer databases from several brands, they should now be able correlate your behavior across these databases.
- People within the email marketing industry are generally calling for restraint. Email Service Providers (ESPs) are all vulnerable to these attacks and the Epsilon breach is just the latest in a series of data security breaches at SaaS vendors.
If you start looking, you quickly find that these breaches occur with depressing regularity. As Laura Atkins points out, the problem is systemic in the ESP industry:
ESPs do not have sufficient security in place to prevent hackers from getting into their systems and stealing their customers’ data.
If you compare ESPs with banks, the approach to security is night and day. Banks generally don’t have these kinds of security breaches, while they are all too common among SaaS vendors. The ESPs might claim that their security is comparable to a bank, but that is empty posturing because they could never afford it.
So if you cannot accept the occasional security breach, what is the alternative to ESPs? The main alternative is to bring email marketing in-house, so that your data never leaves your premises. On-premise applications generally do not suffer from the security problems that seem to plague SaaS vendors. A case in point is that our Connect application has been running in-house at large B2C marketers for nearly 10 years and has never suffered a security breach.
There are two reasons for this track record.
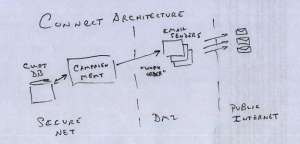
- One reason is the Connect architecture. In Connect, the customer database is kept in a secure subnet and is never exposed to the public internet. The work of sending messages and handling results is done by workers deployed in an exposed subnet. ESPs typically cannot use this kind of architecture because they have to provide access to their clients on the public internet.
- However, the main reason for Connect’s security track record is our customers: they care deeply about data security and don’t trust anyone but themselves to do it right.
Our prediction is that the top brands will re-evaluate their decision to do business with ESPs and many will decide to move the function in house, especially in financial services. If you decide to outsource and compete with a brand that has an in-house ESP, you may eventually be stuck with damage control after the next breach, while your competitor takes market share.

Speak Your Mind